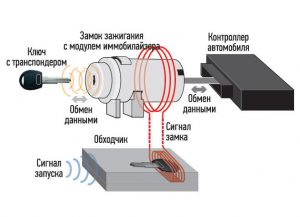
Самое актуальное и обсуждаемое
Популярное
Полезные советы

Важно знать!
9 самых выдающихся обвесов, которые превратят гранту в другой автомобиль
Тюнинг багажника
Для улучшения качеств багажника специалисты по тюнингу рекомендуют производить монтаж спойлера, который создается специально под данную модель авто. Он не только способен значительно...
Читать далее
2021 mini countryman se all4 plug-in hybrid
22 лучших хэтчбека
5 упражнений, которые научат чувствовать габариты автомобиля
7 лучших видеорегистраторов-зеркал с алиэкспресс
6 лучших автомобильных зарядок
2019 dodge charger srt hellcat
15 лучших производителей масляных фильтров
185 регламент гибдд, его плюсы и минусы для водителей
27 оригинальных примеров тюнинга газ-24 «волга»: как дорабатывают легендарную «24-ку»
Лучшее

Важно знать!
3 способа проверить шаровую и почему это стоит сделать как можно скорее
Как проверить шаровую опору
Если вы подозреваете, что с подвеской что-то не так, можно заехать на СТО. Специалисты смогут сказать вам точно, что именно неисправно.
Однако при острой необходимости можно...
Читать далее
2020 mclaren senna
10 лучших семиместных кроссоверов
8 лучших очистителей каталитического нейтрализатора
15 лучших средств для химчистки салона авто
3m, полироль для автомобиля: виды и отзывы о производителе
8 мест, электропривод боковых дверей и цена ниже kia carnival: новый opel zafira life 2021 года
644 административный регламент мвд с изменениями 2019 год
2021 ram 1500 trx
7-местный рамный внедорожник isuzu mu-x 2020-2021
Обсуждаемое

Важно знать!
10 моделей авто, в которых можно спать во весь рост
Выбираем удобную иномарку
Для регулярных дальних поездок подойдут кроссоверы и минивэны с возможностью разложить задние сидения, образовав спальное место на несколько человек. После приобретения такого...
Читать далее
9 автомобилей, которые медленнее остальных ржавеют и гниют
11 лучших полировальных машин
10 лучших линеек антикора
7-местный mitsubishi outlander: все плюсы и минусы кроссовера
5 самых надежных дизельных двигателей-миллионников
2021 jeep gladiator ecodiesel first drive review: do the twist
20 лучших пусковых устройство для автомобиля с алиэкспресс
2021 ram 1500 trx launch edition
10 самых лучших автомобилей для дальних поездок
Популярное
Актуальное

Важно знать!
2 разновидности передвижения на дорогах
Государства, которые изменили движение
Существует немало примеров, когда страны изменяли схему своего транспортного движения. Это случалось по разным причинам: по политическим, географическим или вполне...
Читать далее
126 мотор приора гнет клапана или нет
10 лучших направлений по россии на машине
7 главных причин почему не заводится дизель (на примере мотоблока)
25 крутых и полезных товаров для автолюбителей с aliexpress
15 лучших массажных накидок для автомобильных сидений
5 лучших кредитов с остаточным платежом
15 профессиональных советов по вождению и не только
7 факторов сравнения весты и икс рея
2020 toyota avalon
Обновления
 Статьи
GEELY OKAVANGO vs GEELY ATLAS PRO: Какой выбрать?
Статьи
GEELY OKAVANGO vs GEELY ATLAS PRO: Какой выбрать?
При выборе нового автомобиля, особенно среди множества вариантов на рынке, важно учитывать различные...
 Статьи
Законная купля-продажа автомобиля: необходимые документы и процедуры безопасности
Статьи
Законная купля-продажа автомобиля: необходимые документы и процедуры безопасности
При приобретении или продаже автомобиля важно учитывать не только его техническое состояние и цену,...
 Статьи
Розы в подарок: секреты дарения и ухода за букетом.
Статьи
Розы в подарок: секреты дарения и ухода за букетом.
В мире, где слова часто не могут выразить всю гамму чувств, розы становятся немыслимо красочным языком...
 Статьи
Выбор и покупка авто с пробегом: экспертные советы и надежные решения
Статьи
Выбор и покупка авто с пробегом: экспертные советы и надежные решения
Подробный гид: как правильно выбрать и купить автомобиль с пробегом в 2023 году
Выбор и приобретение...
 Статьи
Роль и функции аварийного комиссара на месте ДТП: подробности и значимость
Статьи
Роль и функции аварийного комиссара на месте ДТП: подробности и значимость
В современном мире, где дорожно-транспортные происшествия являются незавидной реальностью, специалисты,...
 Статьи
Надежность и стиль: Модели Lada — Веста, Приора, Гранта.
Статьи
Надежность и стиль: Модели Lada — Веста, Приора, Гранта.
В мире автомобильной индустрии существует множество брендов, но немногие из них способны претендовать...
 Статьи
Автомобиль Рено Сандеро для города: плюсы и минусы
Статьи
Автомобиль Рено Сандеро для города: плюсы и минусы
В современном мире автомобили играют важную роль в повседневной жизни многих людей, особенно в городской...
 Статьи
Топливная карта «КАРДЕКС ONLINE»: автоматизация оплаты на 12 000 АЗС и АГЗС по России
Статьи
Топливная карта «КАРДЕКС ONLINE»: автоматизация оплаты на 12 000 АЗС и АГЗС по России
Современные технологии активно внедряются во все сферы нашей жизни, и автомобильная отрасль не является...
 Статьи
Hyundai в кредит и лизинг: упрощенная процедура оформления
Статьи
Hyundai в кредит и лизинг: упрощенная процедура оформления
Преимущества и недостатки покупки авто в лизинг
Лизинг: договор найма определяется, как соглашение...
 Статьи
Условия аренды транспортного средства
Статьи
Условия аренды транспортного средства
Одна из самых больших тенденций в области путешествий по стране сегодня - возвращение автомобильных...
 Статьи
Как выбрать машину «рено»: обзор лучших моделей автомобилей этой марки
Статьи
Как выбрать машину «рено»: обзор лучших моделей автомобилей этой марки
Общая информация про RENAULT
Компания «Renault Group» — известная французская корпорация, которая продает...
 Статьи
Что такое незамерзайка и как и куда ее заливать?
Статьи
Что такое незамерзайка и как и куда ее заливать?
Незамерзайка своими руками
Поддержание лобового стекла автомобиля в чистоте является одной из главных...